Chapter 3 Seeing Things of the Internet
“The Internet is the first thing that humanity has built that humanity doesn’t understand, the largest experiment in anarchy that we have ever had.”
— Eric Schmidt at the Internet World Trade Show, New York, 18 November 1999
Among its contributions this thesis presents an alternative approach to widely adopted human-centric perspectives in the design of IoT products and services. Being the locus of this thesis, this requires an exploration of IoT as a design space. In this chapter I present an overview of IoT as a society altering technology, as well as a case for a mismatch between user expectations of what IoT products and services do beyond their immediate task. I use this to build the case for viewing IoT through an alternative perspective than HCD, and then move towards examples in the coming chapters of using speculative design to reveal what the future design of IoT could be like.
3.1 A case for (and against) an Internet of Things
A review of literature around IoT often begins with the origins of the phrase itself. The credit generally goes to a presentation by Kevin Ashton from 1999 that had the phrase in its title (Ashton 2009). Ashton’s presentation was on radio frequency identification protocols (RFID), and its usage in manufacturing processes in industry. Graham and Haarstad (2014, 6) connect the roots of IoT with early attempts at the collection of data through RFID technology, which could explain Ashton’s usage of the phrase in that context. Though Ashton has since attempted to restructure his coining of the phrase, Greenfield (2006, 18) argues for the coming of a zeitgeist for objects that were not before considered as ‘technology’, reclassifying them as housing “information-sensing, -processing, and -networking capabilities”. Since then, IoT has become more commonly placed among concepts relating to ubiquitous computing, often classified as ‘smart’ devices (Kortuem et al. 2010; J. Lindley, Coulton, and Cooper 2017).
The earliest record of an Internet-connected device though goes back to the 1980s. Credited to a Coke vending machine in the Carnegie Mellon University Computer Science Department (Teicher 2018; Madakam, Ramaswamy, and Tripathi 2015). The ‘device’ tracked the duration and temperature of individual bottles of Coke inside the machine. As banal as it might sound, the connected vending machine came out of a want of programmers for the cold caffeinated beverage and their offices being a fair distance away from the machine (Madakam, Ramaswamy, and Tripathi 2015, 166). This origin story is more suited to the state of IoT today as a technology existing among the mundanity of life, but it is also perfect for this thesis as an advocacy for the playful beginnings of transformative concepts and technologies.
3.1.1 Defining IoT
Madakam, Ramaswamy, and Tripathi (2015) begin their review of IoT by breaking down the two components of the phrase: ‘Internet’ and ‘Thing’. The former they classify as a network of networks, and latter, an amalgamation of all “real objects” present in the physical world (2015, 165). They are of the opinion that myriad definitions of IoT are present, each having common threads which they present in the following cohesive definition for IoT:
“[IoT is] an open and comprehensive network of intelligent objects that have the capacity to auto-organize, share information, data and resources, reacting and acting in face of situations and changes in the environment” (Madakam, Ramaswamy, and Tripathi 2015, 165)
Interest in the development of IoT has been primarily seen among large corporations (Greenfield 2006; Madakam, Ramaswamy, and Tripathi 2015; Douglas and Lianos 2000; Chui, Löffler, and Roberts 2010). Its usage has proven to be widespread with IoT-enabled systems emerging in industries such as insurance, chemical production, manufacturing, agriculture, and health care to name a few (Chui, Löffler, and Roberts 2010). The ability to code and track objects using uniquely identifiable information, places IoT as a strong point of interest for corporations with the handling of extracted information, capable of reducing risks and speeding up processes (Ferguson 2002).
Where industries have benefited from the advanced computational prowess of interconnected IoT-enabled systems, the past decade has brought with it significant interest of IoT’s potential in the domestic sector (Coughlan et al. 2012; J. Lindley, Coulton, and Sturdee 2017; Zanella et al. 2014). The term itself has seen iterations coming from different sources all acting as aliases for the broader gamut of an Internet of Things, such as a Web of Things or Internet of Objects (Madakam, Ramaswamy, and Tripathi 2015, 166). A history of IoT aliases is plotted boiling them down to a methodology that utilises machine to machine interaction as a modus operandi at its core with some of the aliases and associations accredit IoT as “Pervasive Computing”, “Ubiquitous Computing”, “Cyber-Physical Systems” and “Human-Computer Interaction”, calling IoT a form of “Ambient Intelligence” present within computing (2015, 166). This presents IoT as a form of technology that is omnipresent and, to a certain degree (or a projected future), omniscient.
3.1.2 Interacting with IoT
Our relationship with technology such as IoT has evolved over time. One may find its roots in early adaptations of science fiction, an understanding that to this day is still present with myriad examples to be found. The modern smart phone and tablet can arguably trace their roots back to their fictional versions in the form of Communicators and Tricoders found in the popular television franchise Star Trek (Bleecker 2010; Akmal 2015). Cinema, television, and creative writing act as benchmarks for imagining new futures in technology through fictional endeavours. Though most of these imaginings fall in the category of fantasy with killer robots or all-knowing devious AI’s, a glimpse of a more tangible version of this is present in academia. One such example is Greenfield’s (2006) Everyware, which discusses forms future technology could take around ubiquitous computing. The book talks of acknowledging the presence of technology capable of consciously processing our daily lives from garments to streets, household objects, and daily mundane rituals, acting collectively to gather information about ourselves for greater purposes.
3.1.2.1 Existing among the mundane
Designers, among other academics, have had a close affiliation with technology and its connection to everyday life; whether that be the domestication of IoT, or, the envisioning of grander schemes of ubiquitous computing (Richardson 2009; Reeves 2012). The vision of the future presented in Greenfield’s book bases itself in Mark Weiser’s famous words, “The most profound technologies are those that disappear. They weave themselves into the fabric of everyday life until they are indistinguishable from it.” (Weiser 1991, 94). Weiser’s famous quote is around the human user surrounded by technology. The disappearing of technology affirms its power and influence on the human through a merging into mundanity. In many regards, design has used the human user and daily life as the focal point in the design process for IoT through an approach called Human-Centred Design (HCD).
Design has always implicated humans at its centre (Love 2000, 293). Predating the Internet, these roots of HCD can be traced back to fields of ergonomics and computer science. Early ISO patents16 showcased standards for what may equate to human-friendly designs. This approach has proven to become a popular choice among designers and scholars in this regard (Giacomin 2014; V. Thomas, Remy, and Bates 2017; Don A. Norman 2002). HCD may act as an umbrella term that accommodates its predecessor User-Centred Design (UCD) (Steen 2011, 45). Today, the word human and user have become synonymous in the design process of IoT and products/services in general with designers opting for HCD as the go-to approach for the design process (J. G. Lindley and Coulton 2017, para. 12). This approach has created a world where IoT-enabled objects and services linger in our peripherals existing in mundanity much like the technology defined by Weiser.
3.1.2.2 Simplicity by design
A core axiom of simplicity is most associated with HCD (Donald A. Norman 1999), and dogmatically exercised in the design of products and services involving human-user-experience. This translates onto the design for IoT where HCD governs how we interact with this technology. Examples can be seen in products such as Amazon’s Alexa or Google’s Nest, presenting minimal ways of direct interaction by design. In his book The Design of Everyday Things Don A. Norman (2002) defines parameters for a user-centred approach to design to include ease, visibility, and the following of natural flows of processing. The examples he gives are of designed items such as chairs, doors, and washing machines, where function and form act in tandem. For instance, a door not designed with torque in mind would be difficult to manoeuvre. Similarly, a washing machine overly designed or improperly labelled would be difficult to operate.
Whilst there is a critique of HCD as a design methodology for IoT at the heart of this manuscript it is not a dismissal of its benefits. Rather, it is the prevailing understanding that simplicity is a necessary requirement of HCD, and more importantly its appropriate usage that is of concern. Donald A. Norman (2016, 34) who is often credited as the originator of HCD has also taken a similar stance towards simplicity in design suggesting both complexity and simplicity existing as conceptual models of “underlying belief structures”. The task of the designer then becomes to acknowledge and appropriate the correct conceptual model as per design problem. Giving the example of moving files into folders on a computer, Norman highlights that while doing so behind the scenes a vast amount of complex computation is undergone while the user plays out a fiction of moving ‘files’ into ‘folders’, allowing the designer to embed a simplified conceptual model of storage through Human Computer Interaction (HCI) into the user.
Furthering this point, Donald A. Norman (2016, 47) continues by explaining how over simplicity is counter intuitive giving the example of a remote control with fewer buttons making certain use cases tedious. On the flip side a remote control with too many buttons would be confusing and excessive, suggesting complexity is a subjective matter as well.
Either logic plays at an anthropocentric view of the design process, and to an extent can create artefacts that function as expected. However, when the presence of ‘intelligence’ is introduced into a product—such as a washing machine or remote control—through IoT, implications emerge of deeper more complex underlying workings presenting a greater challenge for designers to forge appropriate conceptual models for their problems.
3.1.3 The disillusionment of living in IoT
A simplicity-first approach often associated with general understandings of HCD attempts to hide away the interior workings of a product for the benefit of the user. This in a way enacts Arthur C. Clarkes famously cited view of advanced technology being equated to magic (Clarke 1962). Many users will most likely be content with this view, as can be seen from Norman’s example above of ‘files and folders’. This of course is also counter intuitive to core values of HCD such as visibility, feedback, and consistency. “Well-designed objects are easy to interpret and understand” (Don A. Norman 2002, 2). The inclusion of IoT in our daily lives though allows the physical world to transform into an “information system”, promising enhanced capabilities for our already functioning objects with little intervention (Chui, Löffler, and Roberts 2010, 582). This added presence of ever computing AI in products in our surroundings as proposed by IoT, suggests a complex level of interactions occurring behind the fictional conceptual models of our physical interactions with these devices.
IoT and actions happening within remain unclear to human users who are often the centre of these systems for the collection and creation of valuable data. Key properties of human-centeredness highlighted by Norman, thus are not necessarily present in the digital footprint of IoT system design creating a blind spot for users (J. G. Lindley and Coulton 2017; Coulton and Lindley 2019). Some of the points of concern resulting from this blind sport are expressed ahead. Coughlan et al. (2012, 148) are of the opinion that interactions in IoT have yet to explore true human involvement. Donald A. Norman (2016, 41–47) describes himself that it’s unjust to compare the complexity associated with a photo-editing tool with that of a planishing hammer. Each has their own level of complexity which depending on the wielder affords different levels of simplicity; or appropriation of defining simplicity. As mundane objects become networked, our relationships with them as users alter radically.
3.1.3.1 The betrayal of our devices
In his book, Greenfield (2006) also explores the flip side of the equation, suggesting the smart moniker to be deceiving. His view proposes the intertwining of computation in our everyday lives, may breed disturbances:
“When everyday things are endowed with the ability to sense their environment, store metadata reflecting their own provenance, location, status, and use history, and share that information with other such objects, this cannot help but redefine our relationship with such things. We’ll find our daily experience of the world altered in innumerable ways, some obvious and some harder to discern. And among the more significant consequences of this ‘computing everywhere’ is that it strongly implies ‘information everywhere.’” (Greenfield 2006, 23)
Where on the one hand computing of this nature opens doors to creating newly founded interactions—before considered closer to science fiction—this also presents challenges on the emerging fronts of security, ethics, and policy (Weber 2009; Farooq et al. 2015; J. Lindley, Coulton, and Sturdee 2017). Furthermore, accountability for topics such as privacy and the use of data becomes a factor in play when designing for these systems (Boos and Grote 2012).
This brings about the disillusion of IoT in our daily lives. Vamosi (2011) suggests the betrayal of our gadgets and devices when they unintentionally break due to design errors. Giving examples of contact-less interactions with cars, banks, and homes he suggests how technology may have developed a false sense of security among us. This is due to our never-ceasing want for ease in a turn he dubs, “the dark side of convenience” (2011, 25). This is visible in the security risks around IoT which have over the years multiplied 17.
Donald A. Norman (2016, 53) seconds this notion in his own way by highlighting that “assumed trade-offs” between simplicity and complexity are improper applications of design. Taking the earlier example of the remote control he suggests this leading to two understandings, (a) that the goal is to achieve simplicity, and (b) that certain things must be given up in order to achieve it. Continuing on the same note while speaking of a specific Siemens developed washing machine, Norman argues that in the process of automation for the sake of simplification the otherwise accepted simple conceptual model of using a washing machine to wash laundry was complicated by defining the minutiae of the laundry contents to the machine. An otherwise simple process became more tedious in his opinion as with automation the general understanding is trusting in the machine’s judgement.
In Vamosi’s (2011, xvi) terms, we have yet to evolve “survival instincts” around technological fallacies. Solutions surface as often as vulnerabilities through patches and software updates. A further problem comes in the form of excess such as with the case of the above washing machine with ‘extra control’, or with companies offering solutions by overhauling expensive IoT eco-systems 18. Collectively these measures present consumers with difficult decisions around the adoption of IoT.
3.1.3.2 Gathering future technological asbestos
While the above might lead one to assume these issues come solely from a security perspective and the fortification of networks is the solution, in truth design plays a pivotal role in all of this (Vamosi 2011; J. Lindley, Coulton, and Sturdee 2017; Donald A. Norman 2016). With the ever expansion of IoT through networks of heterogeneous interconnected objects and things, the underlying complexities hidden from users arguably through inefficient design choices rise exponentially (J. Lindley, Coulton, and Cooper 2017).
Where IoT does provide benefit in lifestyle and certain aspects of interaction, Internet of Things and smart have become buzz-words for manufacturers to create eventual IoT “asbestos of the future” (Spadafora 2019, para. 2) through products which fulfil rudimentary purposes. These obfuscated interactions do not necessarily come from the need of a user, rather, disguised under convenience they present fundamental problems in the design process of IoT. Take for instance the Quirky Egg Minder Smart Egg Tray19 intended to keep track of eggs in the refrigerator. A selling point of this product is not solely the fact that it can keep track of your eggs, but also, that it can connect to an external IoT hub for one-point access to the device. This implies an additional network where multiple devices, servers, stakeholders, and networks all implicitly interact with an interest in one's refrigerated eggs.
The argument here is not for or against the necessity of knowing the condition of one’s dairy products (though that could be considered), but rather the point raised is that objects such as these surround us with electronic breadcrumbs. These act as key points of entry for not just secure interactions but also insecure and malicious ones. For the sake of (arguable) convenience, how many networks or connections can one truly fortify if it is solely a matter of security?
The smart egg tray is destined to fail in this regard. It along with other similar devices, though designed with good intentions, promote a rudimentary problem in the practice of general understandings of HCD when used for the design of IoT. Weiser’s earlier comment on technology disappearing into the everyday fabric of life is certainly visible in these IoT devices, but they don’t necessarily operate under the truest ideals of design with humans in mind. Where HCD advocates simplicity it also does visibility and feedback which many IoT devices deny with proprietary software, overtly simplified interfaces, or simply a lack of transparency. There is little view of the experience from its perspective for the user, rather, many products are designed with surveillance capitalism in mind. When they could also be imagined to be evolving, cleaner, or secure, traits that benefit the product as much as users by keeping true to human-centred ideals.
3.2 Approaching an alternative perspective for Design in IoT
Hungarian painter and professor for the Bauhaus School László Moholy-Nagy, wrote that “ultimately, all problems of design merge into one great problem: ‘design for life’” (Moholy-Nagy 1947, 42). What differentiates a normal refrigerator with an IoT-enabled one is what Pierce and DiSalvo (2017) consider a ‘networkification’ of a world outside of the Internet, presenting with it levels of agency and value not originally associated with the device. Through IoT designers redefine aspects of living. Objects connected in IoT present themselves as simple solutions to mundane problems, yet, they house complex designs emerging from this networkification creating a complex problem space.
Obscuring hidden workings through general applications of HCD under the guise of ‘simplicity’ may be welcome in some cases as many human-users could benefit from the lack of excessive information. Yet this obfuscation, paradoxically, also accredits the aforementioned security hazards in IoT, further opening avenues for similar concerns (J. Lindley, Coulton, and Cooper 2017, para. 1).
Our hyper-connected world is governed by assemblages of mediated data collected and processed through the various devices and systems in place around us. Simplification of such a complex system may only agitate the problem space further when challenges such as societal, economic, or environmental are faced around IoT (Coulton and Lindley 2019, 466).
To see this in perspective, J. G. Lindley and Coulton (2017, para. 2) give the example of a smart meter intended to control heating in a confined space. The associated value for this device drastically changes between stakeholders involved. As a consumer, one might be inclined to reduce the amount of energy used. Yet, as the energy provider they would be motivated to maximise profits; with or without data collected from the meters. Whom is the smart meter designed for? What attributes should a designer focus on for this device? Should it be the efficiency of use? Stakeholder engagement and interests? Or effects on the environment?
Figure 3.1: This appropriation of the illustration by J. G. Lindley and Coulton (2017), suggests that the perspective through which users see their world is not necessarily the same for IoT devices.
Certainly, concerns around privacy and transparency are of importance when considering HCD. Through the examples mentioned previously, and countless others strewed across the Internet, privacy is often the first casualty when designing for IoT. Many of the highlighted concerns appear to be solely a matter of transparency, though excess information is equally a subjective issue when designing. Certain systems might not need their underlying operations to be deemed extra information, equally some designs could require it. When perspectives differ so drastically for an IoT product and service design (Fig. 3.1), then how does one approach this design space?
3.2.1 Changing perspectives
The appropriation by Buchanan (1992, 14) of “wicked problems” in design are often considered the baseline for justifying methods in design research. The argument presented, is that problems addressed by design are far more complex and indeterminate with no immediate solutions existing a priori, ergo, understanding the situation becomes as important as formulating a solution (Gaver 2012, para. 24). Examples of this are problems such as climate change and solutions presented under the umbrella of sustainability. This is why design researchers often employ methods from diverse disciplines converging together to create a focal point around a subject matter they have invested in through an act of “innovative repositioning” (Buchanan 1992, 11). What this means is for design researchers to conduct their research they must accept the fact that the solution will lie in resituating the problem. In our case, for the design of IoT we need to change our perspective.
The complexity of the situation emerges partly from our innate trust in technology, but also perspectives exercised through HCD. Ironically, one of the most notable and quoted figures in the argument for HCD Donald A. Norman (2005, 14) has also argued against an anthropocentric approach to design, proposing an “activity-centric” approach instead. On the matter of designing for IoT, J. G. Lindley and Coulton (2017) present a case in favour of alternative design approaches to HCD saying that perspective plays a large role in how one may view IoT.
All the examples presented above create an argument for the ‘things’ in IoT as being more than physical objects. Besides their physicality they include abstract concepts such as data, algorithms, software architecture, policies, and business models, to name a few. Each of them defining these concepts in different ways. The interrelations of these different elements fuel the problem of complexity, and as such is how a smart television could infuse paranoia,20 or a baby-monitor might also serve a criminal activity 21. J. Lindley, Coulton, and Cooper (2017) are of the opinion that extreme use of generalised conceptual models of simplicity associated with HCD, may unintentionally detriment the adoption of IoT.
3.2.2 Metaphorically speaking
Arguments are presented for expanding the scope of HCD to include elements such as the environment and objects (V. Thomas, Remy, and Bates 2017; Coulton and Lindley 2019), and even fantasy and lore (Rose 2015). This acknowledgement of abstract entities as actants in an IoT network expands on the broader perspective for design. One way of seeing IoT is through metaphor as suggested by J. G. Lindley and Coulton (2017, para. 3), presenting the concept of metaphorical “constellations” for IoT.
This argument suggested by Buchanan (1992, 12) of innovative repositioning through design practice incorporating diverse disciplines in this instance, is conducted through the use of metaphor to understand alternative perspectives better. IoT is not a stranger to the use of metaphors. Different sources express interacting in and among IoT comparable with non-digital experiences (Cila et al. 2017; Rose 2015; Romero, Pousman, and Mateas 2008). The infamous quote of technology as magic can be viewed as a way of describing something like IoT akin to sorcery for the less informed. Rose (2015, 52) discusses this approach further by seeing IoT housing “enchanted objects”, capable of enhancing our daily experiences akin to magical artefacts from lore. Though his view could be argued as still anthropocentric in certain regards, it proposes an alternative viewpoint. One where these objects are given importance and value beyond their utilitarian function, embodying them with a higher essence to serve their human-users. In the coming two examples I will build a case for viewing IoT through metaphor in order to understand it better from alternative non-human perspectives.
3.2.2.1 Enchanted experiences
Rose (2015, 111) presents the case of an umbrella inspired by the magical sword Sting from The Hobbit by J.R.R. Tolkien. Where Sting informed Bilbo Baggins of nearby danger, Rose’s umbrella informs him of whether it’s about to rain. Though a simple premise, the interaction becomes an enchanting one capable of pulling the user into a playful world where umbrella’s converse with their users about the weather. Furthermore, it establishes a deeper existence for the device disconnected from the human.
One could argue that our devices are always enacting themselves in our background lives. But where the enchanted umbrella differs is in its anticipation of use: “Objects that anticipate their use; know when they’re needed” (Rose 2015, 111). This is not collecting data because it can be collected, rather, it is obtaining data as a result of meaningful interactions. One that not only is important to the user but establishes a strengthened presence of the device.
Where the IoT egg tray could be shrugged off as an item of jest just like the USB ghost tracker from my past, the enchanted umbrella incorporates a playful experience in a manner that elevates the device by design. Through a metaphor of enchantment the magical aspects of IoT, or underlying complexity, is approached in a human-centred way providing a meaningful interaction beyond that of a regular umbrella. Arguably, the complexity is not made visible in this instance but for the end-user it remains an intimate interaction with a simple conceptual model, glowing umbrella equals rain as opposed to the series of side interactions to check the weather before leaving. This also highlights the umbrella’s awareness of things out of the human user’s control or knowledge. Rose gives many such examples that present IoT-enabled objects comparable to magical artefacts from fantasy fiction, making them metaphorical representations of magic and simplifications of otherwise complex interactions.
3.2.2.2 A faceless shapeless Internet
A further definition of the Internet is provided by Pierce and DiSalvo (2017, para. 1) who refer to it as “shapeless and faceless”, attesting to the benefit of defining IoT through perspectives of metaphor. The notion of a constellation design creates relations in IoT that are “independent-but-interdependent” (Coulton and Lindley 2019, 467). The user is removed from the centre of the equation and becomes one piece in a larger puzzle with services, stakeholders, business models all residing in their respective dependencies (Fig. 3.2). In this light, perspective becomes important as what is of value changes according to what is viewed and by whom.
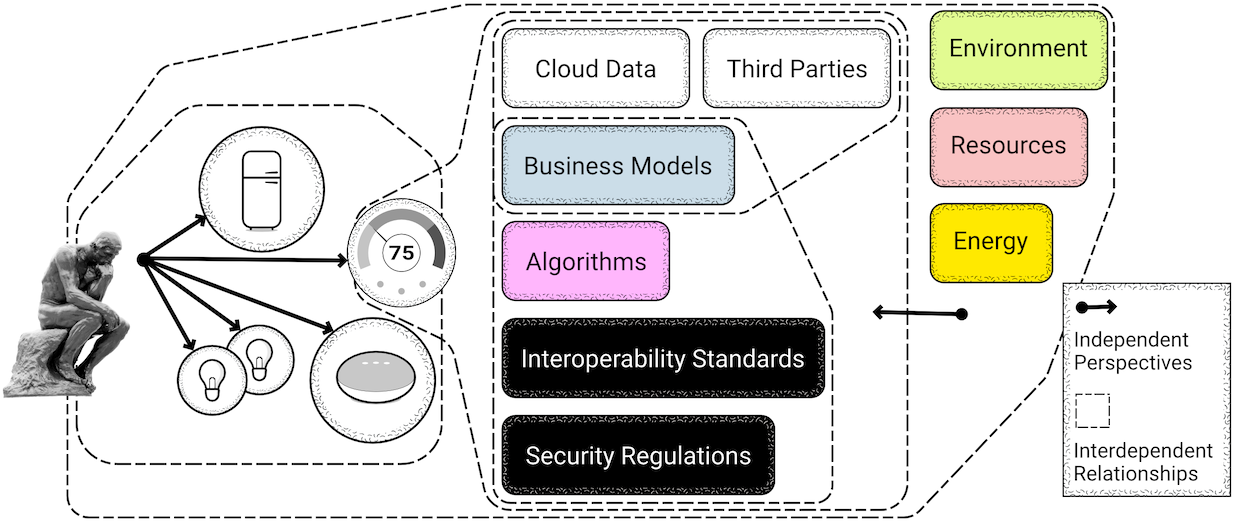
Figure 3.2: Seeing IoT through a metaphor of constellations reveals individual perspectives and dependencies in relation to the observer.
More so, one must understand that the things in IoT differ from those in our daily lives. Whether we see it as enchantment through Rose (2015) or betrayal as Vamosi (2011) suggests, IoT objects are different from non-IoT counterparts. Partly because of their abilities (magical or otherwise), but also because of the workings behind the illusion they present 22. Paraphrasing Pierce and DiSalvo (2017, para. 1), they are as shapeless and faceless as the Internet they exist in. To further this point we can see the comparison by Coulton et al. between a wired telephone to its IoT alternative, the smart phone, illustrating the difference in regular things and IoT-things:
“The wired phone is a single purpose device, connecting into the phone network, which itself is a complex but highly sanitized and controlled system. The smartphone on the other hand is a general-purpose computer, imbued with a range of sensors, connected to the Internet, running user-installed software. It so happens that it also makes phone calls and, for historical reasons, is primarily referred to as a ‘phone’. This is analogous to the contrast between ‘things’ and the IoT.” (Coulton and Lindley 2019, 468)
The metaphor of a constellation allows for this contrast to be seen more clearly. A wired telephone exists for a singular purpose making/taking phone calls, and thus serves simpler stakeholders which can be drawn out in a linear fashion of telephone company to user and back. Of course the telephone company and user are under the influence of third-party effects such as government policies, this model is less influx than a digital network as I will explain. The smart phone serves multiple stakeholders from the fact that it is more than a device for making phone calls. Among these stakeholders include but are not limited to the user, network providers, manufacturers, government policies, applications in use, third-party manufacturers and advertisers, and so on. So, a linear model is not possible. Through this assemblage of independence and interdependence, a series of “networked ecologies” (Coulton and Lindley 2019, 467) are created. One can see them as collections of interacting bodies, depending on each other to form a cohesive interaction. Where immediate interdependence is viewed in basic interactions like user input, others are less obvious but just as important. Coulton and Lindley also give the example of smart televisions which log user activity. Users information is not simply used to tailor the viewing experience but is passed on by the manufacturers to third parties for targeted marketing based on those interactions.
IoT devices are not solely owned by their users just as the telephone lines are shared between the provider and client. The difference between these services comes when seeing that unlike traditional networking abilities IoT devices also may incorporate other types of networked things. This may include other devices, interactions with businesses, communications with government authorities, or unsolicited interactions with third-parties. Metaphorically speaking, IoT networks exist as constellations of interacting bodies with clusters of independent and inter-dependent interactions each affecting the other in a daisy-chain manner.
The alternative perspective presented has been termed “more-than human centred design” (Coulton and Lindley 2019, 478) to look beyond the precedence of an anthropocentric view. It utilises elements of speculation and a large part of philosophical debate to understand how one can experience concepts such as IoT from different perspectives. By removing the human centre in this view, one can focus on the networked ecologies housing the different stakeholders and their various interactions. This allows for a broader perspective, which was before given solely to the human-user. Thus, in order to acknowledge alternative approaches towards HCD for the design of IoT, one must acknowledge the independent and inter-dependent perspectives of the things in IoT, their lives, objectives, and intentions.
3.3 Conclusion
From the above understanding of constellations in IoT the human user is not the centre unless its place in a wider ecology is examined, such as between user and device or user and internet service provider. The more expansive the ecology, the more the ‘centre’ is realigned. All the while these networks remain hidden from the human user.
In light of the playful attitude towards research presented by this thesis if taking the view of IoT as enchanted objects as posited by Rose (2015), then one can see these hidden workings as background processes of magic; or how the illusionist manages to hide away information. Examples such as these, present an alternative case for viewing IoT as constellations where actants rely on their interactions with others. The metaphor may stage the setting for understanding the illusion better. In Chapter 9 I go into much more detail exploring these illusions generated between user and device through philosophical musings, but before going into that there is a lot of ground to cover in the coming chapters.
This is a case for misaligned conceptual models to generalised understandings of HCD in practice. Simplification does not necessarily lead to ease of use and could equally unearth unintentional flaws in design, particularly when considering IoT where beyond security measures concerns such as privacy and ethics are at stake. A more-than human approach encompasses elements of design that elevate the experience beyond mere servitude. Shying away of underlying workings of IoT for the sake of simplifying use to highlight device servitude, inadvertently leads to further complexity. Visio’s lack of regard for user privacy is a haunting example among the plethora of others befallen to ignorant or at times nefarious design choices in IoT.
Objects in our vicinity exist out their vicarious lives, a philosophical concept. This way of viewing IoT through a lens of philosophy is the driving argument of this manuscript proposed through its playful attitude towards research. A philosophical discourse around understanding this alternative perspective to HCD will be highlighted in the next chapter to act as the main driver of metaphor for viewing IoT differently.
References
HCD’s six guiding principles are defined under ISO 9241-210:2010 as projects that include designs based on an explicit understanding of users, tasks and environments; an involvement of users throughout the design process and development; is driven by user-centred evaluation; involves an iterative process; addresses the whole user experience; and includes multidisciplinary skills and perspectives within the design process.↩︎
In 2019 India faced a staggering 20% jump in cyberattacks on IoT devices making it the most attacked nation in that quarter. For more information, see: https://www.thenewsminute.com/article/india-saw-most-cyberattacks-iot-space-last-quarter-subex-report-106989.↩︎
In the start of 2020 Sonos announced a discontinuation of ‘legacy’ IoT products bringing about outrage from consumers who had spent fortunes in the smart home Sonos eco-system. For more information, see: https://www.wired.co.uk/article/sonos-outrage-legacy-speakers.↩︎
For more information, see: https://www.smarthome.com/quirky-ge-egg-minder-smart-egg-tray.html.↩︎
For more information, see: https://www.wired.com/2017/02/smart-tv-spying-viziosettlement/.↩︎
For more information, see: https://www.healthline.com/health-news/baby-monitors-can-be-hacked.↩︎
In Chapter 9 I go into much more detail on how these illusions manifest between user’s anticipations with IoT and the actual workings of IoT.↩︎