Appendix
The Internet of Things Board Game Explored
The Internet of Things Board Game was a lengthy endeavour into understanding the creation of unique procedural rhetoric in play around philosophy, design, and IoT. All aspects of the game would be too difficult to communicate as it went through 14 iterations with some being entire overhauls in design and rhetoric. So as to not derail the focus of this thesis, this information is kept as supplementary content as the true rhetoric of the game can only be understood by play. This special section is therefore devoted to illuminating as much of the game as possible in its latest iteration (14 at the time of writing).
For ease, this section is presented as a game manual with additional footnotes explaining the reasoning behind certain decisions. The detailed background process of reaching this iteration is explored in the journey of Chapter 8.
In addition to the game manual presented here, the game may also be experienced online as a video playthrough. As of writing this manuscript the playthrough is intended to give a brief idea of how the game operates. This online content may be updated in the future with further information regarding the operations of the game. The playthrough may be experienced here:
Backstory
Imagine a world in a parallel realm not very different to your own, in a time not too far into the future with people not unlike you. Imagine a place shining with technological brilliance driving a society offering peace, tranquillity, efficiency, and ultimately futures full of happiness and hope: Welcome to Sol on the distant world of Atlas Prime. A place where technology and human are two sides of the same coin, where the physical meets the digital and paves the roads you walk on.
Just around the turn of the century, the forerunners of The Algorithm praised it as a way to move forward. One system to control all and ensure daily safety bringing about a technirvana. Soon heard of in magazines, e-zines, and newspapers everyone spoke of it and expected others to join. However, what was meant to be a means of watching over and securing loved ones evolved into an obsession of control as The Council was born!
Initially proposed as a way to streamline matters of government, The Council proposed using The Algorithm to gain access to all affairs of life. From family trees to bank details, to how many bags of tea were left in people’s pantries. Suddenly data was the new currency, and one digital signature was all it took to fetch, analyse, and upload information to a hive-mind network.
Now, people are born into a world where they are digital cookie distribution machines dropping bits and bytes of information about everything they do. The once free cities of Atlas Prime have all been following the image of Sol. Over time The Algorithm evolved to include other versions, secret incremental updates that gradually tightened its grip on everyone and everything. The past, a distant blur of memory that The Council’s data-hungry algorithms have almost entirely wiped out exists in the form of rogue code woven into the digital fabric of the free cities inhabitants. Lost advertisements, Memes, Gifs and messages commented into program code have been circulating in the shadows of Tor networks; those that still are out of reach of The Council’s deep search engines. They whisper a prophecy of the counter system called, the DataBox.
The DataBox is said to give people back power, essentially blocking out Council attempts at foraging data. By giving people control over what data can and cannot be in the reach of others, DataBox is the nemesis The Council have been fearing. As such, they’ve created their countermeasures. Although a series of algorithms meant to hunt out rogue code, its ferocity of action with a seek and devour reputation towards data cookies has given it infamy as the Cookie Monster!
Now with the enemy having unleashed its hounds upon whosoever attempts to stand against them, a ragtag group of vigilantes have taken up the mantle to fight back. Welcome to the Resistance! The last bastion against an invisible enemy! You and your party members will traverse between the tangible and the intangible Internet to take back what is yours. But be warned, The Council is ever watching. Botnet’s and Spyware are but the tip of the iceberg as they intend to stop you, or worse, have you assimilate!
Afraid of potentially losing all their influence and control, The Council have begun work on another upgrade to their Cookie Monster algorithms. An update proposed to eliminate all links to code related to DataBox on any connected network. Deceptively named The Crumble this increment should successfully end any chance for resisting the reach of the Cookie Monster. As part of the Resistance, you can’t allow that and must fend off any daemons thrown at you establishing a secure encrypted network.
Tread lightly, there are Privacy bombs and traps everywhere! Be prepared lest you get spotted in virtual floodlights. The digital landscape is no longer a peaceful one so keep an eye on that Threat Tracker. Will you build your secure networks in time for The Crumble?
Game Objective
The Internet of Things Board Game is a 2–4 player cooperative board game where players work together against amassing digital threats to build a secure network amongst themselves. Create digital links as you traverse physical spaces on the board and secure them by deploying Databoxes equal to twice the number of players. Build all the Databoxes and win the game!
Play Setup
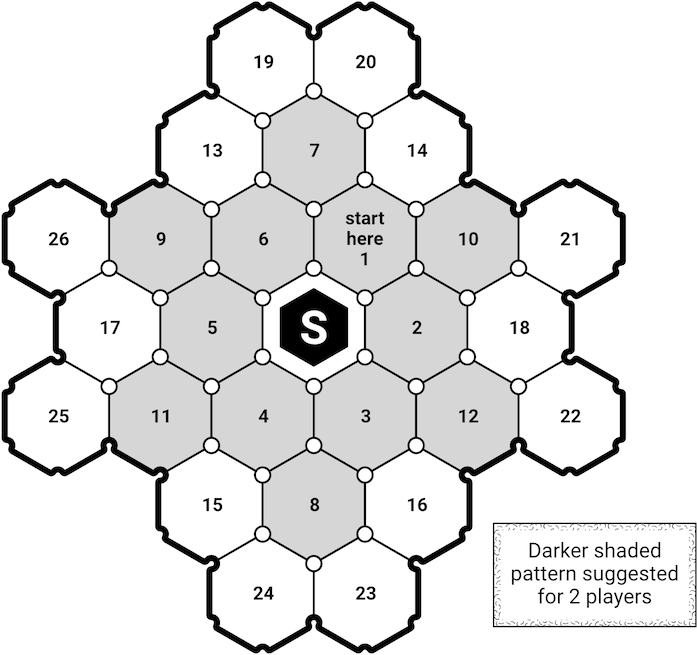
The board is prepared according to the number of players. First, place the Server tile in the middle. Next, separate Insecure Tiles (see B.6) and Regular Tiles into separate piles upside down and according to the number of players from Table. B.1, take the top tiles from each pile to make a tile deck. Return the remaining tiles to the box, and shuffle the tile deck placing them in a pile upside down. Now pick tiles from the top of the deck and place them following the numbers in Fig. B.1. Each tile of the board is now a different space that players can navigate. Once placed tiles cannot be moved.
Table B.1: Number of players and tile formations.
| 2 |
9 + 3, or, 8 + 4 |
2 (2), 2 (1) |
| 3 |
7 + 5, or, 6 + 6 |
2 (2), 4 (1) |
| 4 |
19 + 7 |
4 (2), 4 (1) |
Next, ignoring the Server randomly pick tiles (see B.8.2) and follow Table B.1 to add Vulnerability tokens (see B.12) to them infecting those spaces. Add double tokens from the table first, then single. Players now select an Avatar (see B.7) to play with, taking that avatars board and placing the corresponding standee on the Server tile. Any items associated with selected avatars are collected by players, as well as one Primary item each (see B.9.1.1). Players set their avatar to their starting settings and finally, place the Threat Tracker (see B.17) to the side of the play area agreeing upon a difficulty level for play. Starting with whoever last used an Antivirus on their devices, play may now proceed clockwise.
Phases of Play
Each player’s turn comprises of two phases, an Actions Phase, and Risk Phase . During the Actions Phase a player gets to do up to 2 actions per turn (unless they are Delayed, see B.7) allowed out of the following actions:
- Move: Players can move in any direction up to their Speed level (see B.7).
- Find: Roll for Observation (see B.8) over spaces with an EYE icon to draw one item from the Items Deck (see B.9).
- Trade: If sharing a space with a player trade any number of items with them.
- Rest: Recover 1 Sanity OR attempt to resolve any Daemon cards in hand (see B.15).
- Connect: Return items in hand or use items in spaces to make a Connection (see B.10).
- Discard: Remove 1 item in hand from play.
- Ability: Use player or card Abilities (see B.7).
- Resolve: Attempt to clear a space of Issues (see B.13).
- Deploy: Spend 2 actions to attempt a Privacy card (see B.9.3), if succeeded deploy a Databox (see B.16).
- Skip: Skip an action.
After spending actions the player must enter the Risk Phase by rolling for Security (see B.8). In the game, this is often called Rolling for Risk or conducting a Risk Check. If they succeed play continues to the next player. If they fail the following is done in order:
- Place a Vulnerability token (see B.12) in the space occupied and any further connected spaces.
- Draw a card from the Risk Deck and follow the card in order top to bottom (see B.9)
- Do risk checks on all items in hand using the new dice-count from the drawn card (see B.9).
- If the drawn card requires other players to act as well, do so accordingly
- The player ends their turn, next player begins with their Action Phase.
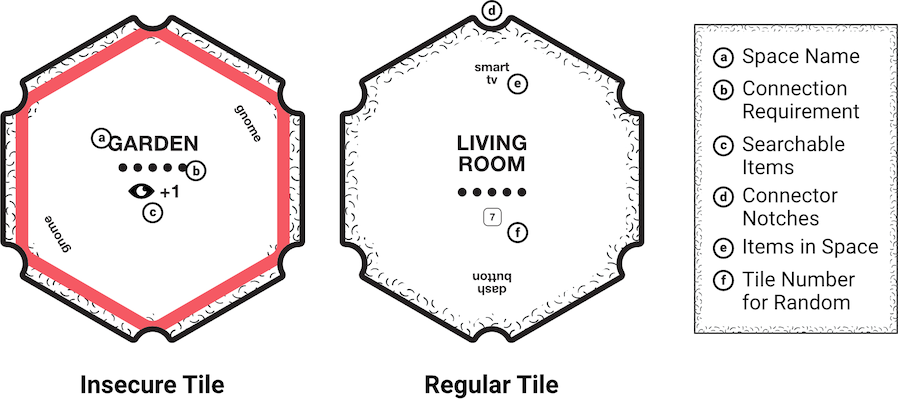
Understanding the Tiles
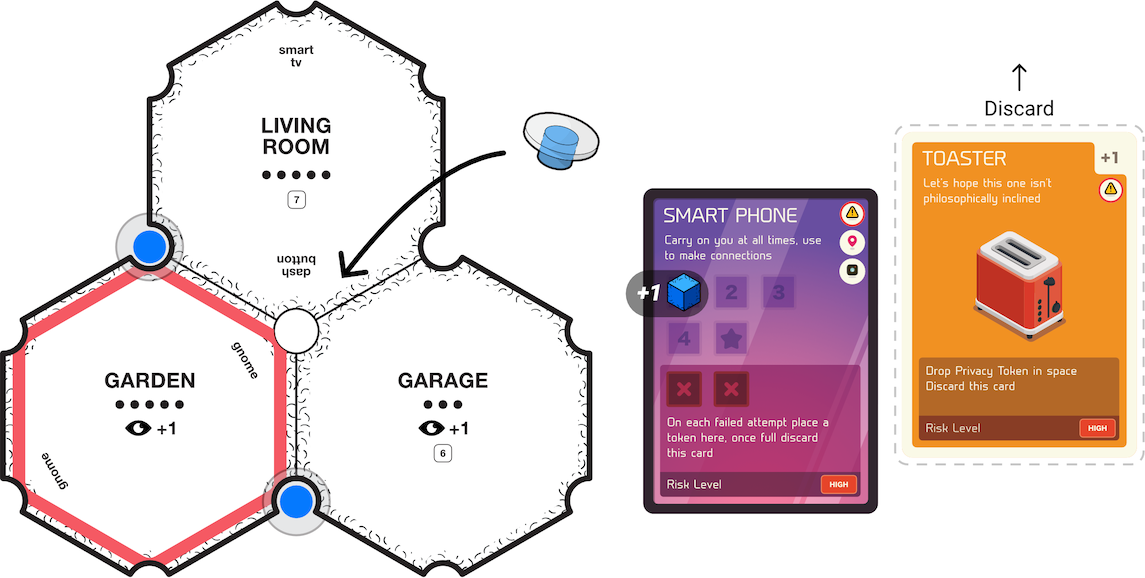
There are 2 kinds of tiles in the game, Regular Tiles and Insecure Tiles (Fig. B.2). They both function similarly, except for one thing: Insecure Tiles force players to Roll for Security twice during the Risk Phase, meaning they could cause it twice. This only occurs if a player decides to stop their Move action on an Insecure Tile. Insecure Tiles are recognised with their darker borders. Tiles are all named after physical locations such as a living room, kitchen, etc. and act as physical spaces. Spaces also signify connectivity using the notches in the corners (see B.10). See Fig. B.2 to understand the different parts of each tile. Each space, subsequently, has a connection requirement which needs to be fulfilled before it can be secured by turning into a Databox.
Some tiles have items players can connect to within them (see B.10). Generally, when a player connects a space they place a Connection Token in the open space next to the present item. Be careful when making these connections! If you end up connecting with an Insecure Tile you have to Roll for Risk.
Tiles also show as dots how many connected spaces are needed before deploying a Databox (see B.16). Players may use their Find action to draw cards from the Items Deck (see B.9.1) on tiles that have an EYE icon (some tiles allow for more than 1 item to be drawn indicated by a number next to the icon).
Avatars
Players may play as different characters or avatars in the game. Each avatar comes with their own standee and board for keeping track of skills. Avatars each have unique abilities which players can use during play as actions. Certain avatars have Passive abilities which are always active, for instance, Spook can always clear all Vulnerability tokens in a space in one action.
Avatars have skill levels defined by their Speed, Sanity, Security, Observation, and Coding skills on their boards, with their starting skill levels highlighted (Fig. B.3). Speed is denoted in the top right corner of the avatar board and refers to how many spaces a player may navigate up to in their turn. As the game progresses these skills rise and fall, and players may keep track using provided blue and black tokens. To keep track of reduced speed, add black tokens next to the Speed skill. For all other skills (except Sanity) when a player must permanently reduce their skills such as after the Effect of a Risk card (see B.9.2), black tokens can be placed as reminders. Each number on the tracks (except for Sanity and Speed) represent the number of dice a player can roll for that skill. For instance, in Fig. B.3 Spook has a Coding skill of 4 meaning the player controlling Spook can roll 4 dice when asked to roll for Coding. However, as Spook also has 2 black tokens on his Coding track the player only gets 2 dice to roll.
Rolling Dice
There is a lot of dice rolling in this game! The general rule while doing most dice rolls is:
\[
d6\left( \text{SkillLevel} \right) \pm Modifiers
\]
Modifiers are any cards or events that alter the number of allowed dice during play (see B.9). Skill level is the level of the skill asked to roll for. For instance, Spook has a Coding skill of 3, when asked to roll for Coding the player controlling Spook gets 3 d6 to roll with, however, if they also have a Health Monitor item they get an additional d6 (see B.9.1.2).
Having multiple dice in a roll is important as it increases your chances of passing. A pass is if the player gets a 5 or 6 during the roll on any 1 die. Alternatively, players may lower the difficulty of play by including 4 as a pass. Anything besides will be considered a fail and depending on the situation (which often will involve a card or token) the corresponding Effect will come into play (see B.9).
Doing an Attack Roll
Sometimes players will have to get aggressive and attack the board. When doing an Attack Roll, players roll for Coding against a d20 going to the opponent (sometimes cards make players attack each other). Dice are rolled together subtracting the total value of player dice from the opponent. The opponent always wins a draw. To win players must get a value higher than the opponents unless the following rolls occur:
- A 1 on the d20; this is an instant kill; the player wins immediately irrespective of what they rolled.
- A 19 or 20; this is an instant hit from the opponent making the player face consequences if present. If no consequences (such as an Effect, see B.9), the player must back away 1 space losing either 1 Sanity or lowering a skill by 1. This rule is irrespective of getting a higher value from the dice, but if the roll was higher the player may roll again after taking damage.
Randomisation
During play, players will often be asked to randomise an action. This is done by rolling a d20 and referencing the tile with the corresponding number. Each Regular Tile has a number printed from 1–20. Random actions may never reference an Insecure Tile.
Understanding and Reading Cards
There are 4 decks of cards in the game: Items, Risks, Privacy, and Daemons. Cards in the deck usually have a Function and an Effect, with the latter represented in a darker shade. Each card is read top to bottom and often have numbers or icons in the corners which trigger other Effects.
Items Deck
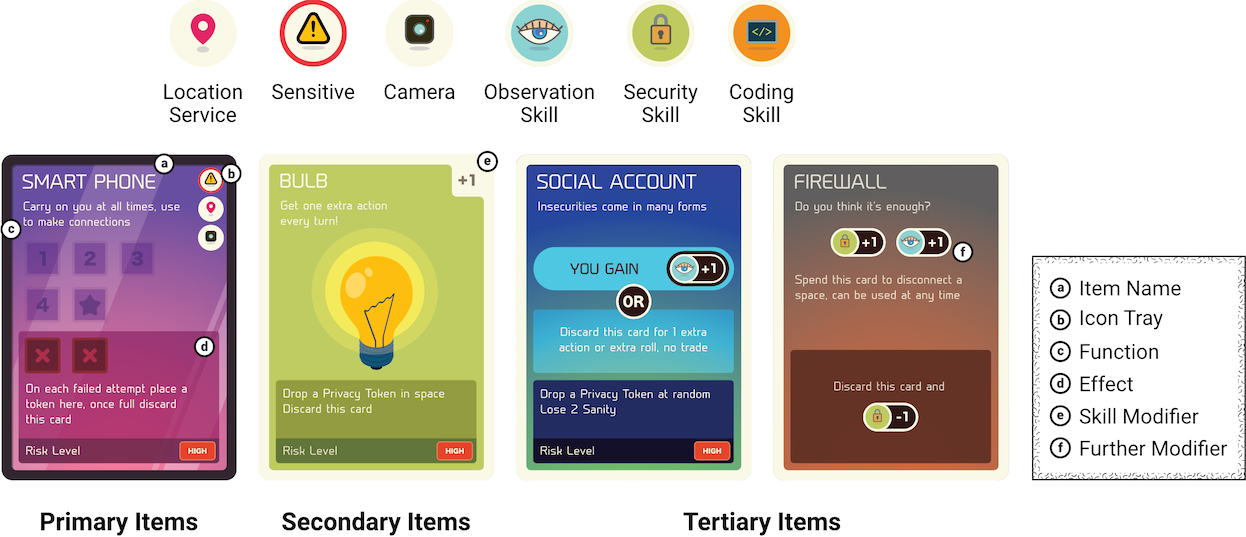
This deck is comprised of three kinds of items Primary, Secondary, and Tertiary each with their functionality (Fig. B.4). Players may carry cards in hand up to a hand-limit of 5 cards. Certain events and cards may change this number during play.
Primary Items
These are smart phones and tablets, and their Function is to make connections in the game. They each have a connect limit (see B.10), and upon completion players get a bonus action for every completed Primary item in hand. For instance, if there are 5 blue Connection tokens on a players smart phone item, for all future turns including the current one they get 3 actions instead of 2. Although, if at any point they lose that Primary Card or have to reduce tokens on it, the bonus is lost.
As an Effect activated upon failing the Risk Phase, players must do a Risk Check on all tokens present on the card. For each failed roll, players move that token to the Effect portion of the card. When no more spaces are left there the card is discarded and the Threat Tracker (see B.17) advanced by 1.
Secondary items
These are different everyday IoT objects that players discard to make connections on the board using their Primary items. The Function of each Secondary item is between activating icons used by other cards (often Risks) and increasing skill levels as modifiers according to the colour of the card; orange for Coding, blue for Observation, and green for Security. Each time a player fails a Risk Check during their Risk Phase (see B.11), the Effect of that card is played out.
Tertiary items
These are either Accounts or Buffs both acting as benefits if players keep on hand, but come with associated higher risks if they become insecure (by failing a Risk Check). Tertiary items often act as modifiers when calculating dice counts for rolling. Furthermore, these cards usually may also be spent for an immediate bonus function. Players may spend these cards and take advantage of bonuses at any moment in the game. Once spent, the card must be discarded unless specified.
Risks Deck
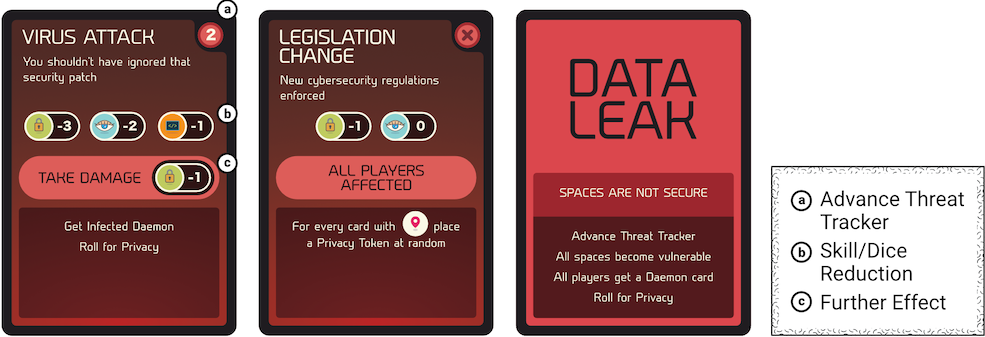
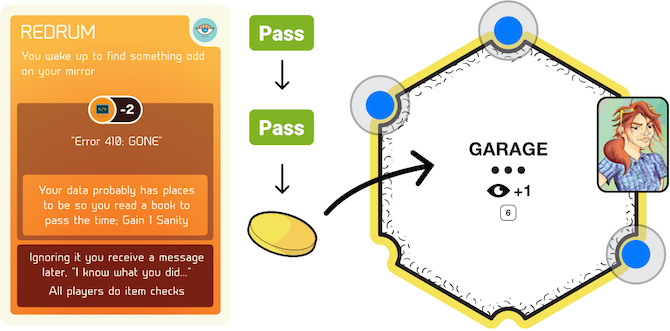
This deck is full of all that can go wrong in the game! Each time a player fails the initial roll for Security during the Risk Phase, the top card is drawn from this deck and its Function played out. First, the number in the corner denotes how many steps forward the Threat Tracker moves (see B.17). Second, players collect dice equal to the totals of each skill represented on the card following the subtractions. The new dice roll is then used for each subsequent Risk Check (see B.11) in that phase. Finally, the player(s) takes any associated damage followed by the cards Effect immediately. Besides the regular Risk cards, there are also Data Leaks. These cards affect ALL players immediately triggering all Privacy tokens (see B.13) and advancing the Threat Tracker (see B.17).
Privacy Deck
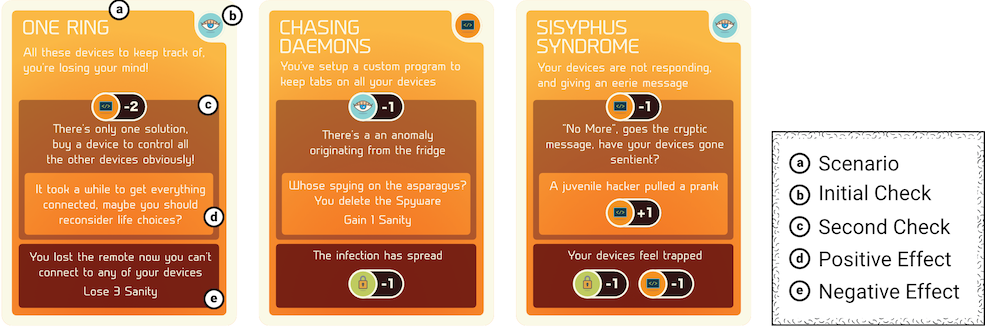
Cards from here are invoked when players attempt a Deploy action for a Databox (see B.16) . Players must successfully navigate the different conditions presented stepwise otherwise face consequences. These cards require players to first roll according to the icon in the corners to see if they may proceed. If at any moment players fail a dice roll, they must execute the cards negative Effect at the very bottom and discard it. However, if they pass the initial roll, they enter the second step often requiring a more difficult skill check. Upon passing that as well, players may execute the positive Effect of the card along with deploying a Databox. For instance, the Chasing Daemons card (Fig. B.6) has players roll for Coding to be able to move forward to its next step, which further requires an Observation minus 1 check. Upon passing, this card gives the player not only a Databox but also +1 Sanity. If at any moment in this card the dice rolls fail, the negative Effect is played, and the player loses 1 Security skill discarding the card from the game.
Daemons Deck
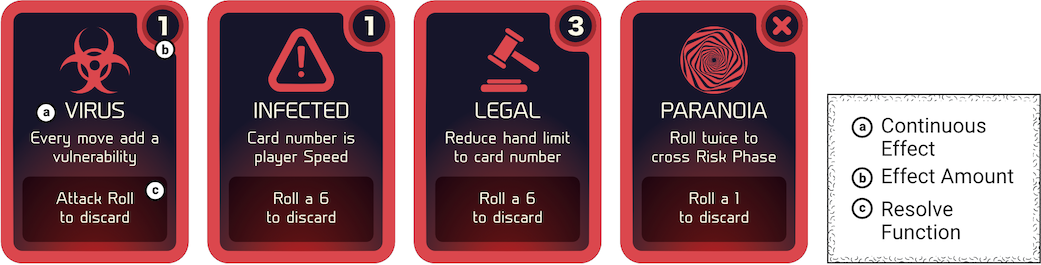
These cards act like software daemons where it gets its name from. They are not drawn by choice and instead issued by other cards as constant Effects upon players; often reducing their skills and abilities (Fig. B.7). Many cards have an Effect Amount in the corner linked with the card. For instance, if a player receives a Virus Daemon, they must add 1 Vulnerability token on every space they move to. Daemons are stackable and may only be removed by doing a Rest action (see B.15) and attempting the cards Resolve portion.
Making Connections
Items collected throughout the game may be traded for Connector tokens (Fig. B.8). This is an important part of play. To win players need to deploy Databoxes which can only be done in spaces that have reached their connection requirements. There are a few prerequisites To make a connection. First, a player must have a Primary Item on hand (see B.9.1.1). Second, players need to navigate to a space with an empty notch. Finally, connections can only be made by either discarding a Secondary Item (see B.9.1.2) from their hand or using an item in the space.
Items in spaces are shown on the tiles and can only be connected to the notch they occupy. When players discard an item from hand to make a connection, they add a blue Connection token to their Primary item. Each new Connector makes a new Connection token on their card. These cannot be removed once added thus players must acquire new Primary items to make further connections if they reach their connection limit. As a bonus, using in-hand items to cover notches meant for items in spaces in the same action, gives the player two blue Connection tokens together to place on their Primary item. Finally, all notches on a tile may be used for connecting, even those on the outer rim of play.
Conducting Risk Checks
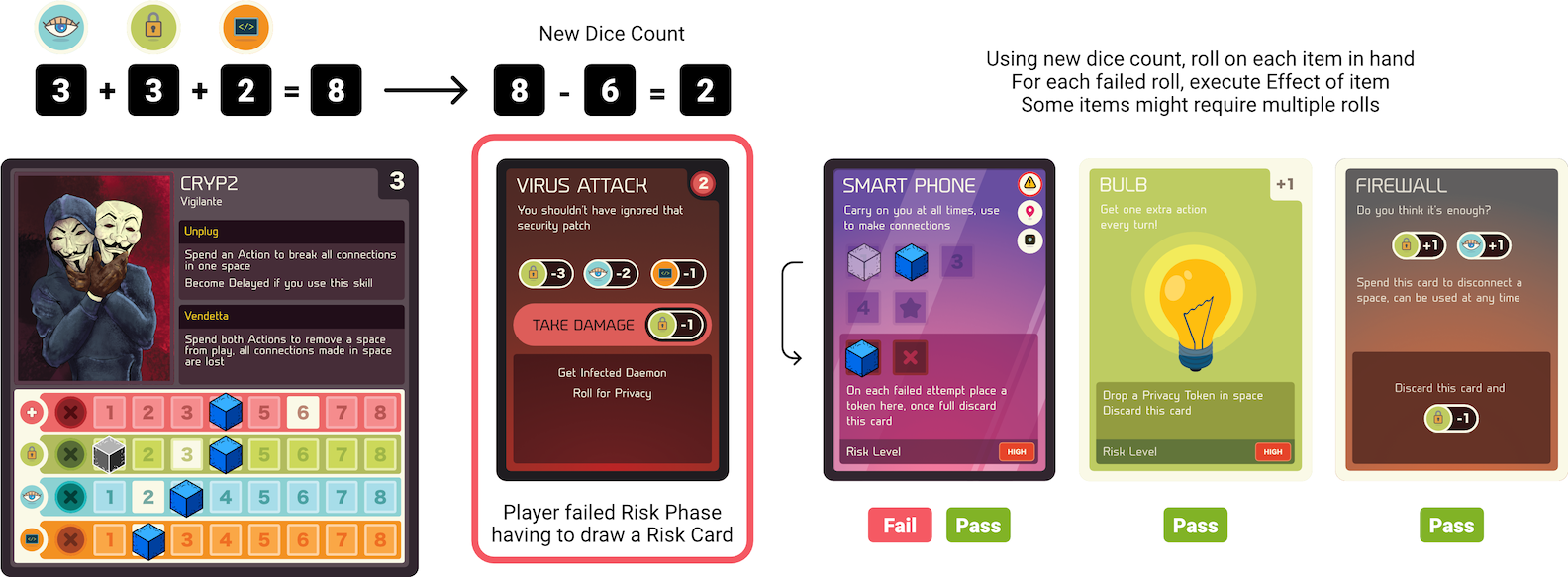
During play (particularly the Risk Phase) players will have to undergo Risk Checks. These are done by rolling Security on each item in hand. Failing any of the checks means executing that cards Effect portion (which could further trigger a secondary Risk Check). During the Risk Phase, these checks are more elaborate with the dice count being decided by the drawn card (Fig. B.9) . For instance, the Virus Attack card (Fig. B.5) tells the player to do the following in order:
Move the Threat Tracker ahead 2 spaces.
Collect the total dice count of the player’s Security, Observation, and Coding skills.
Subtract that dice count by 6 to a minimum of 1 dice.
After using that new dice count to roll on all items in hand, reduce player Security skill by 1 as damage.
Then finally play any Further Effects on the card. In this case, the player takes an Infected Daemon (see B.9.4) and rolls for Privacy (see B.13).
Tokens
Table B.2: There are a number of tokens in the game representing different functions and affects.
| Round Connector Tokens |
*(F)** Shows connections between physical spaces |
| Blue Connection Tokens |
(F) Denotes connections made during play on cards |
| Orange Vulnerability Tokens |
(F) Denotes low-level insecurity issues within a space or item; (E) Converts into a Threat token if more than 2 in one space |
| Black Threat Tokens |
(F) Denotes high-level insecurity issues within a space; (E) Each Threat moves Threat Tracker ahead by 1 (see B.17) |
| Privacy Tokens |
(F) Ticking time bomb that churns out Vulnerability tokens after certain events; (E) If the number of Privacy tokens exceeds the number of players the game is lost |
| Block Tokens |
(F) Denotes a disconnected space; (E) If Block tokens exceed the number of players the game is lost |
| Databox Tokens |
(F) Marks the space as a Databox; (E) Step closer to victory (see B.16) |
Resolves and Other Actions
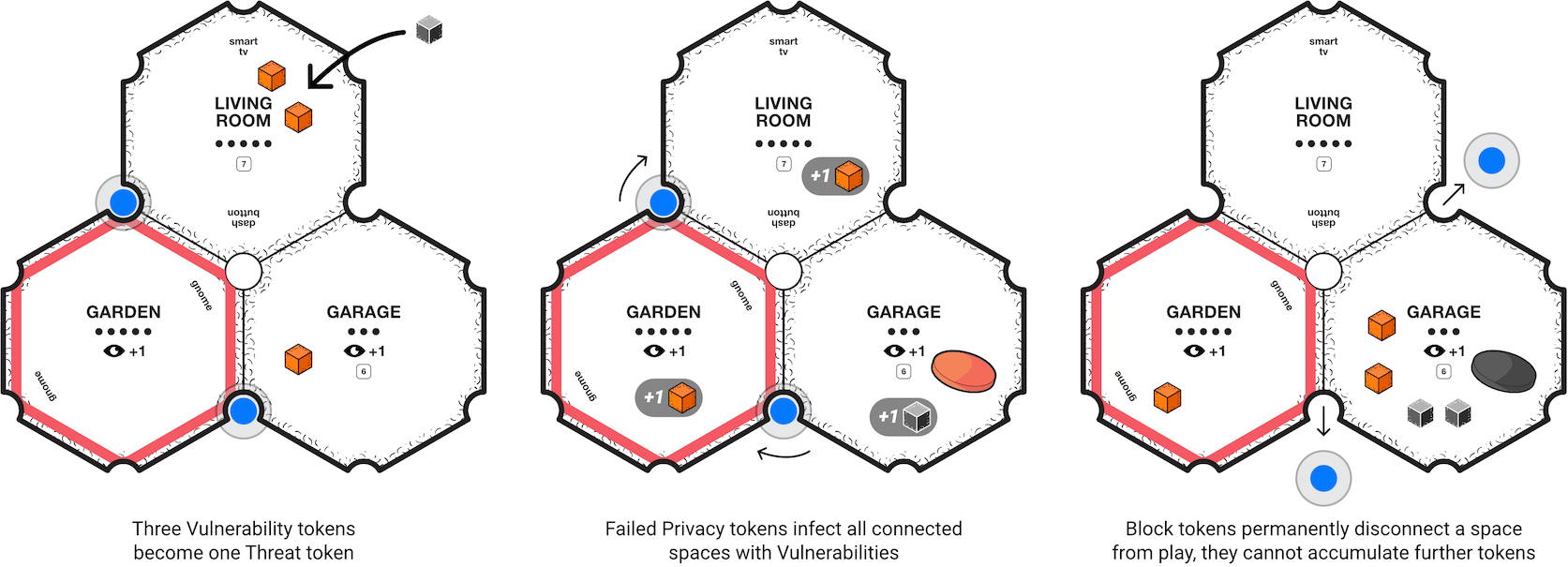
When players are on a space or card that has an issue needing to be resolved (Vulnerability, Threat or Privacy tokens), they may encounter them as a Resolve action often by rolling for a skill. The interactions of the different tokens are shown in Fig. B.10.
Vulnerability: These tokens are easier to remove and simply take an action to clear 1 from the space occupied, unless a players avatar or other cards allow them to resolve multiple.
Threats: If a space has 2 Vulnerability tokens, a third token would replace the 2 with a black Threat token. They are persistent, advance the Threat Tracker (see B.17), and require an Attack Roll to resolve (see B.8.1).
Privacy Tokens: When instructed to roll for Privacy the player rolls 1d6 for each Privacy token in play; 1–4 is a fail, 5–6 is a pass (follow the difficulty level of the game, see B.4). If the player fails on any of the tokens the following happen in sequence: a Threat token is placed in the space occupied by the player; all adjacent spaces of the failed Privacy token receive Vulnerability tokens; all connected spaces from the Privacy token receive Vulnerability tokens. If during this action (or any other) the Server receives a Vulnerability or Threat, all spaces connected to the Server with Connector tokens will also receive Vulnerability tokens. Privacy tokens are removed through an Attack Roll (see B.8.1). If a Privacy token falls on the Server, players must resolve it within 1 round otherwise the game is lost (see B.18).
Block Tokens: Some cards, and in dire circumstances certain players, may Block a space. Place the Block token on the tile and remove any Connector tokens from it as well. These cannot be resolved; they are permanently disconnected spaces from the board. They do not accumulate any further tokens and any tokens present within if removed do not affect the Threat Tracker.
Being Delayed
At times players may become Delayed during play. This is not something they would do at will but be forced by cards. Delayed players skip the next Action Phase, but must endure the coming Risk Phase of that turn. To indicate a Delayed player, place their standee on its side in the space they occupy. After completing the Risk Phase, they may continue as before.
Resting
As an action, players may Rest and regain 1 or more Sanity. During this players are also allowed to resolve any number of Daemon cards ONCE in that action. To do that, they must follow the Resolve Function on a Daemon card (see B.9.4). Certain events and cards may allow players to do this function multiple times.
Databoxes
To win, players must secure spaces with Databoxes equal to twice the number of players. These are special tokens that may only be placed in space after the connection requirements are fulfilled AND a player has a successful Deploy action (Fig. B.11). When a player is ready to deploy a Databox, they spend 2 actions to draw the top card from the Privacy Deck following its conditions (see B.9.3). Upon successfully navigating the card, a golden Databox token is placed in the space marking it as secure. No further tokens of any kind may come into a Databox. As a bonus, each Databox deployed will recede the Threat Tracker (see B.17) by 1 and if players manage to deploy a Databox in an Insecure Tile, they may recede the Tracker by 2!
Threat Tracker
The Threat Tracker (Fig. B.12) keeps track of when The Crumble occurs signifying a victory for the game. To stop that happening, players must attempt to finish before it reaches the end. The Tracker moves forward in two ways:
- When a Risk card or other card moves it forward.
- When a new Threat token appears in play.
Certain card events may recede the Tracker during play. Players may only do so themselves by deploying a Databox (see B.16).
End of the Game
The game ends with either the players winning or losing to The Council (the board). Players may only win if they deploy Databoxes equal to twice the number of players. The Council wins if ANY of the following comes true:
- All players are Delayed together (see B.14).
- The Threat Tracker reaches the end (see B.17).
- There are Privacy or Block tokens equal to more than the number of players (see B.13).
- There is a Privacy token on the Server and it’s not resolved within 1 round of play.